Azure AD custom security attributes
Microsoft have launched in public preview the Azure AD custom security attributes and user attributes in Attribute-based Access Control (ABAC) conditions build on the previous preview of ABAC conditions for Azure Storage.
What is a custom attribute? They are key-value pairs that can be defined in Azure AD and assigned to Azure AD Objects, such as users, Enterprise Applications (Service Principles), and Managed Identities.
Why use custom attributes? Custom Attributes allow you to add some business-specific information to an Azure AD Object, this could be a user’s cost center or the business unit that owns an enterprise application. By using a user attribute, it allows the ability for ABAC conditions within Azure Role Assignments.
What are the use cases? There are a number of use cases around Azure AD Custom Attributes and in my opinion, a much-needed feature to be seen in Azure AD.
What do you need to enable Azure AD custom security attributes? You need Azure AD Premium Licenses
Let’s take a quick look at how you can manage attributes, use them to filter Azure AD objects, and scale access control in Azure.
Step 1: Define Attributes in Azure AD
The first step is to create an attribute set, which is a collection of related attributes. For example, you can create an attribute set called “Sales” to refer to the attributes related to the sales department. The second step is to define the attributes inside the attribute set and the characteristics of the attribute set. For example, only pre-defined values are allowed for an attribute and whether an attribute can be assigned a single value or multiple values. In this example, there are three values for the region attribute—Ohio, California, and New York—and a user can be assigned only one of the three values.
Step 2: Assign attributes to users or enterprise applications
Once attributes are defined, they can be assigned to users, enterprise applications, and Azure-managed identities.
Once you assign attributes, users or applications can be filtered using attributes. For example, you can query all enterprise applications with a sensitivity level equal to high.
Step 3: Delegate attribute management
There are four Azure AD built-in roles that are available to manage attributes.
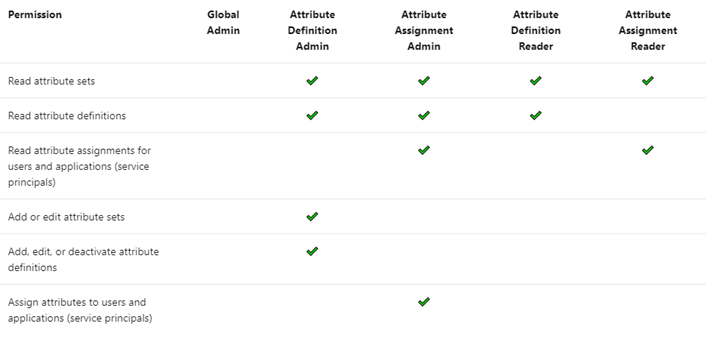
By default, Global Administrators and Global Readers are not able to create, read, or update the attributes. Global Administrators or Privileged Role Administrators need to assign attribute management roles to other users, or to themselves, to manage attributes. You can assign these four roles at the tenant or attribute set scope. Assigning the roles at tenant scope allows you to delegate the management of all attribute sets. Assigning the roles at the attribute set scope allows you to delegate the management of the specific attribute set.
Step 4: Achieve fine-grained access control with fewer Azure role assignments
With Resource attributes (for example blob index tags), you will need to create a role assignment for the user and add the relevant conditions. However, this means that you will need to create as many role assignments as there are users.
By using User attributes along with resource attributes, you will be able to create one role assignment with all users in an Azure AD Group and add an ABAC condition that requires a user’s category attribute value to match the blob’s category tag value.
To summarise, user attributes, resource attributes, and ABAC conditions allow you to manage access to millions of Azure storage blobs with as few as one role assignment.
Auditing and tools
Since attributes can contain sensitive information and allow or deny access, activity related to defining, assigning, and unassigning attributes is recorded in Azure AD Audit logs. You can use PowerShell or Microsoft Graph APIs in addition to the portal to manage and automate tasks related to attributes. You can use Azure CLI, PowerShell, or Azure Resource Manager templates and Azure REST APIs to manage ABAC conditions in Azure Role Assignments.

